Wannakey, the Wannacry decryption tool
Appeared in May, 2017 Wannacry infected more than 200.000 computers in approximately hundred countries. This message of ransom joins to a software which is going to code your data to live as a parasite so on your computer until that the “ransom” is settled …
Abstract
If you have been connected to the Internet for the last two weeks, you must have heard about Wannacry, the ransomware which infected hundreds of thousands of computers around the world.
Basically, the malware targets all the Windows releases, even if Windows 10 has been quickly patched. It encrypts the files hosted in your computer and asks you for paying a ransom of $300 in order to get the decryption key.
Fortunately, the French researcher Adrien Guinet developed a decryption tool that is able, under certain conditions, to decrypt your files.
What is Wannacry ?
Wannacry is a powerful ransomware that emerged on May 12th, 2017. Transmitted by a pdf file sent in a phishing mail, it has infected more than 200,000 computers in nearly 100 countries around the world.
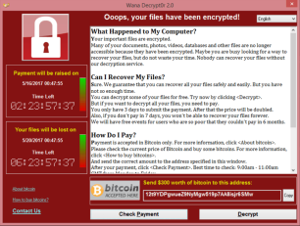
It is a malware composed of two separated modules. The first one exploit a vulnerability in Microsoft’s SMB (Server Message Block) protocol called EternalBlue, got from the NSA leaks, which permits it to spread on every reachable machine in the local network. Then a second module encrypts all the files it fouds in the computer and renames them with a .WNCRY extension and places a lock screen with the ransom image as you can see below.
A kill switch found in the worm
It turns out that, before trying to spread through the local network, Wannacry first tries to reach this initially unregistered domain name: www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, and spreads only if it is not reachable. When it has been found out, this domain name has been registered, what temporary prevented the worm to propagate himself on the network, but not to encrypt the files in the initial targeted machine.
Several hypothesis exist on why Wannacry creators integrated this kill switch in their malware. One of them is that they deliberately make it to be able to stop their own “monster” in case of problem.
Although this kill switch contributed to slow the expansion of the worm, we must be carefull because a new version of the malware, Wannacry 2.0 was quickly released without this domain name check.
Wannakey
If your computer runs on Windows XP, Seven, 2003, Vista or Windows Server 2008 and you see the lock screen above, you should look at Wannakey. Developped by the French researcher Adrien Guinet, this tool will retrieve the private key by looking for the file wcry.exe in your computer.
Actually, Wannacry uses the RSA (Rivest, Shamir and Adleman) encryption algorithm, which is based on the mathematic problem about the factorisation of big prime numbers. For that, it uses the Windows Crypto API and it turns out that CryptDestroyKey and CryptReleaseContext do not remove the two prime numbers used to generate the couple of encyrption/decryption keys before freeing the memory.
So Wannakey could be able, particularly if you did not restart your computer yet, to find those prime numbers in wcry.exe file and to decrypt your computer.
- Phone: +33 (0)1 85 09 15 09
- Email: incident@httpcs.com
